Patch management should be on top of your top priorities as a Sysadmin and as a Security Analyst you should also be on top of the latest patches released by Microsoft, along any 3rd party software that your endpoints are running.
The challenging aspect of patching servers is that if you don’t have any kind of patching solution (such as SCCM), the patch management process might become somewhat manual and not flexible as we’d like (Think maintenance windows, scheduled reboots, etc). In addition, Sysadmins or server owners might not patch their servers because they think it will “break” their systems/applications or simply they forget. The point of this article is to accomplish somewhat the same functionality we get from SCCM when it comes to scheduled installs, and suppressed reboots. Let’s get to it!
Before we move on to my suggested patching process for Production servers, I am assuming that you or your organization does the following:
- You have a test environment and patches are tested
- You have talked to the Sysadmin and server owners to ensure this process works for them
- You have a policy that states how often Production Servers will be patched and what times they can be rebooted (let’s call this maintenance window)
- You don’t have SCCM (Which is why you’re probably reading this article), if you do have SCCM disregard this article and take advantage of it.
Since we know that Sysadmins or server owners are forgetful, let’s try to automate this process. Just how in SCCM you would schedule a deployment at a certain time, but not reboot it until say a Saturday morning, we will try to accomplish something similar.
Here’s our scenario:
On Patch Tuesday (2nd Tuesday of the month) when Microsoft releases their updates, our WSUS server will auto-approve new updates that will be downloaded by these servers. 7 Days after the updates were released, a scheduled task will trigger at 5 a.m. that will run a PowerShell command which triggers the installation of those updates without rebooting them).
Our assumption here is that 7 days will be enough to know if any patches broke our “test systems”, realistically your organization might wait a few weeks or months to ensure their test environment is normal post-updates. Additionally, if you don’t want to automatically download the updates from WSUS (say there’s a bad update), you can also delay the downloading of those potential “bad” updates.
Let’s get started.
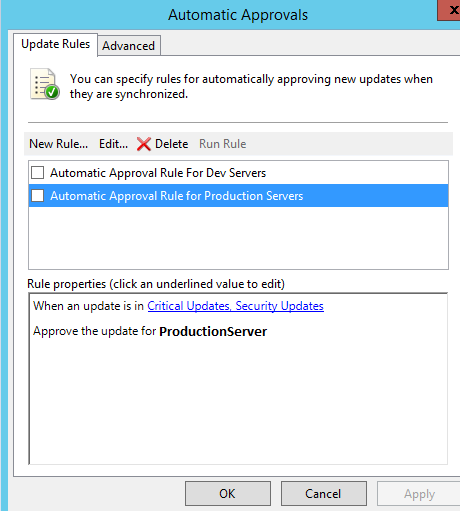
WSUS Prerequisites: Automatic Approvals
On WSUS, we will automatically approve Critical Updates & Security Updates.
Navigate to Options > Automatic Approvals >
WSUS GPO for Production Servers
We will create a GPO that will be applied to production servers, it will accomplish the following:
- Point our endpoints to our local WSUS server
- Automatically enroll our endpoint to a specific group in WSUS (ProductionServer)
- Configure our endpoints to “Download Updates from WSUS automatically)
- Prevent our endpoints from installing updates automatically
Browse to your GPO and edit.
Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Updates
Look for the following options and double click:
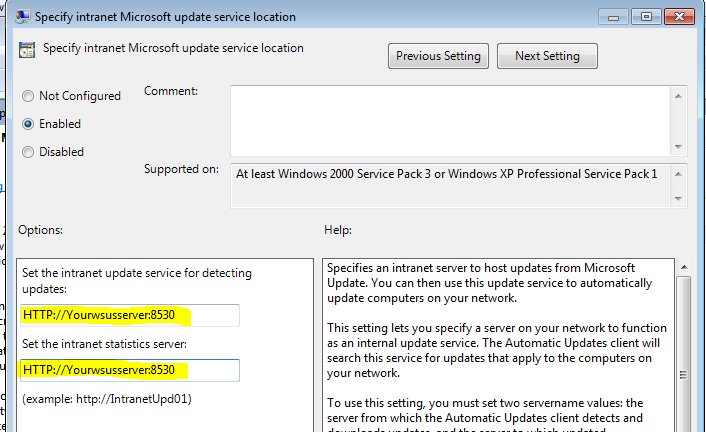
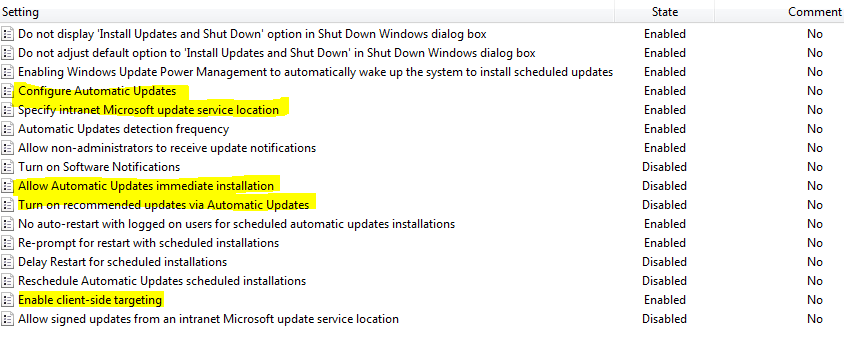
1. Point our endpoints to our local WSUS server:
Specify Intranet Microsoft Update service locationSet to Enable and enter your WSUS URL. e.g. HTTP://Yourwsusserver:8530
Specify Intranet Microsoft Update service locationSet to Enable and enter your WSUS URL. e.g. HTTP://Yourwsusserver:8530
2. Automatically enroll our endpoint to a specific group in WSUS (ProductionServer)
Enable client-side targetingSet to Enable and enter your WSUS target group e.g. ProductionServer
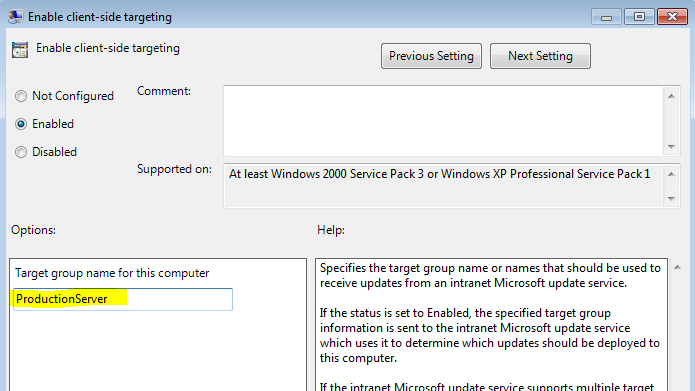
This will automatically assigned your endpoint to a specific WSUS group which allows any new domain-joined production server to be placed in the correct group and help with the automated process.
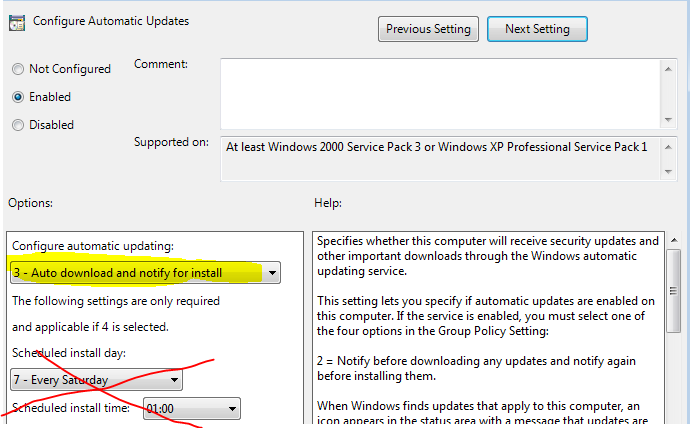
3. Configure our endpoints to “Download Updates from WSUS automatically)
Configure Automatic UpdatesSet to Enable and Option 3- Auto Download and Notify for install(set whatever scheduled day and time as they won’t matter unless you choose option # 4)
4. Prevent our endpoints from installing updates automatically
Disable the Allow automatic Updates immediate installation option.

5. Here’s the remaining settings you may choose to follow or not. The highlighted ones are a “must” for this use case.
PSWindowsUpdate – Powershell Prerequisites
Now that you’ve setup your WSUS to automatically download the updates to our production endpoints but NOT install them automatically, we can now setup PSwindowsUpdateDeployment. PSWindowsUpdate is a powershell module to manage Windows Updates on a Windows system. There are available functions that are available on the site, so read over it if you get a chance.
Step 1: Create Powershell Windows Update install batch file
First create a batch file that will be placed on the root domain folder that is accessible to each domain client.
Here’s the batch file:
Save as PSWindowsUpdate.bat
What does it do?
The batch file will copy the PSWindowsUpdate which contains the Powershell module prerequisites files to the following location: C:\Windows\System32\WindowsPowerShell\v1.0\Modules\. Next there is a 15 second delay just to give us time to ensure that the files were copied (You may change this, in case your network is slow). Lastly, there is a Powershell command that imports the PSWindowsUpdate module (Import-Module)
Step 2: Download the PSWindowsUpdate.zip file from the Official Microsoft Site and extract locally.
Step 3: Create a folder on your domain that will be replicated with other domain controllers (in my example: apps), and copy the following there: PSWindowsUpdate.bat, PSWindowsUpdate.zip
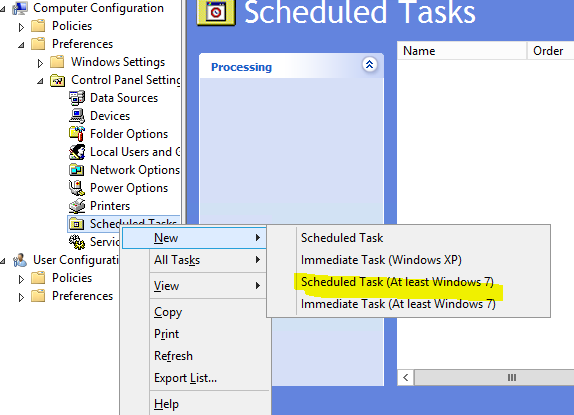
Step 4: Creating a Scheduled Task to deploy the PSWindowsUpdate powershell module
Right click your domain OU and
- Create GPO in this domain, and link it here
- Provide a name (PSWindowsUPdate Deployment) , hit OK
- Right click your newly created GPO Sysmon Deployment and select Edit
- Navigate to Computer configuration > Preferences > Scheduled Tasks
- Right click Scheduled Tasks and click on Scheduled Tasks (At Least Windows 7) (This should work for Windows 7,10 Server 2008/2012)
Under the General Tab set the following:
Under the Trigger Tab click on New
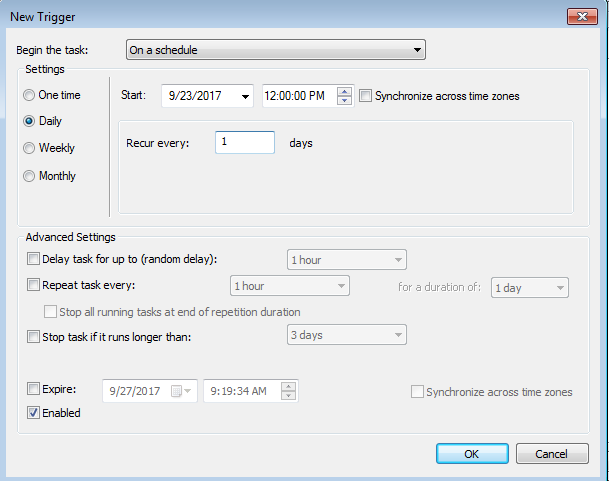
I’ve set mine to run daily at 12 p.m, you may schedule this to fit your needs.
Under the Actions tab click on new
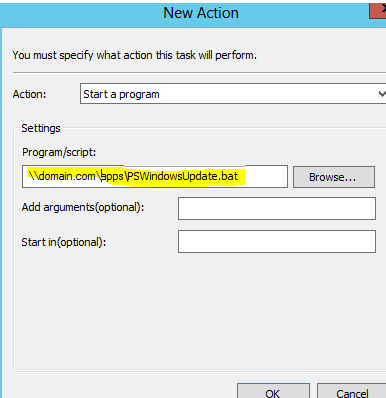
Browse to your domain location and select the batch file we created. Hit OK when done.
Optional step: Under the Settings tab, you can check the
Allow task to be run on demand (This will allow you to manually trigger the scheduled task on an endpoint when you login. It helps with initial testing).
Allow task to be run on demand (This will allow you to manually trigger the scheduled task on an endpoint when you login. It helps with initial testing).
Next, we’ll schedule the actual installation of the windows update.
PSWindowsUpdate: Scheduling the patching installation
Quick recap – At this point we have accomplished the following:
- Created GPO to auto-download updates to our endpoints
- Suppressed any kind of automatic installation or reboots
- Copied and installed the PSWindowsUpdate module on our endpoints
We will now create a “Scheduled task” that allows us to trigger the installation of the updates that were downloaded locally to our systems.
On your existing GPO or new GPO do the following:
Step 1: On your GPO navigate to: Computer Configuration > Preferences > Control Panel Settings > Scheduled Tasks
Right-click Scheduled-Tasks and do New > Scheduled Task
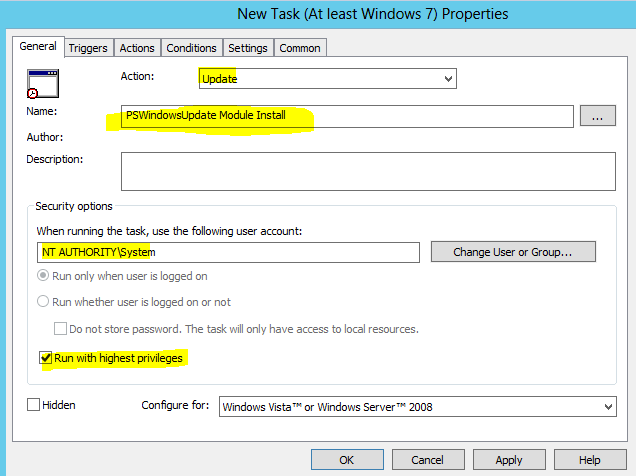
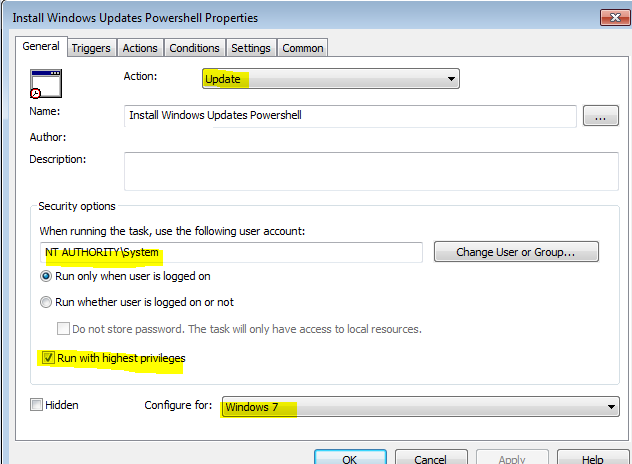
On the General tab, set the following options:
Action: Update
Use the following account: NT AUTHORITY\System (Or if you have a specific service account with rights to perform the scheduled task)
Run only when the user is logged on
Run with highest privileges
Use the following account: NT AUTHORITY\System (Or if you have a specific service account with rights to perform the scheduled task)
Run only when the user is logged on
Run with highest privileges
On the Trigger tab add New
Set to your own preferred time
Set to your own preferred time
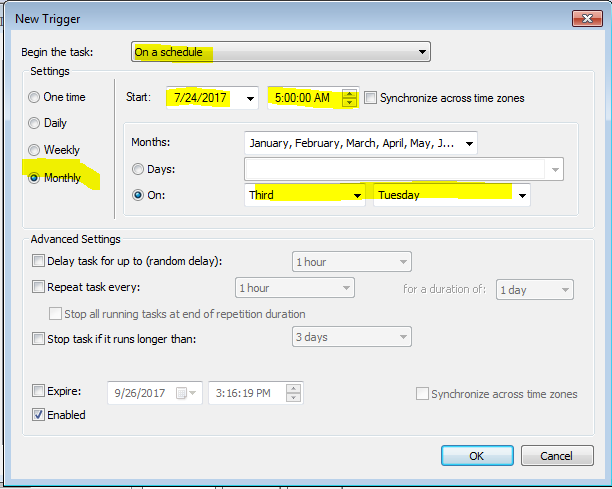
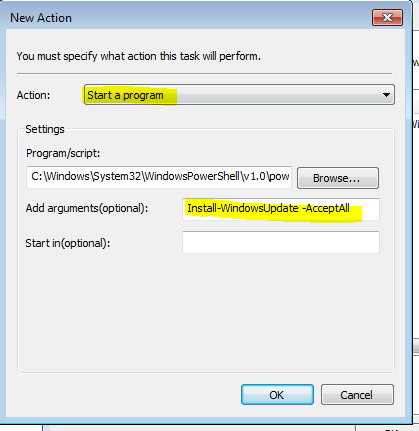
On the Action tab do New
Action: Start a programProgram/Script: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exeAdd Argument(optional): Install-WindowsUpdate -AcceptAll
Optional step: Under the Settings tab, you can check the
Allow task to be run on demand (This will allow you to manually trigger the scheduled task on an endpoint when you login. It helps with initial testing).
Allow task to be run on demand (This will allow you to manually trigger the scheduled task on an endpoint when you login. It helps with initial testing).
This is it! now apply this GPO to your Production OU; however, first test this with a few test servers to ensure that it works as intended.
Final notes
Once you apply the Auto-download updates, you can go back to your endpoint and run the following powershell command to ensure that your files were in fact downloaded. This will ensure that you are in fact receiving updates from WSUS
Get-WUInstall -MicrosoftUpdate -IgnoreUserInput -WhatIf -Verbose
You may also check if there’s any new updates available from the WSUS server:
Get-WUList -MicrosoftUpdate
and lastly, if you’re testing the module manually, you may trigger the updates yourself by running the following:


No comments:
Write comments